Deploying in Amazon Web Services
Introduction
ScaleOut StateServer can be licensed from the AWS Marketplace for use in Amazon Web Services. Using Amazon Web Services, you can quickly deploy many instances of the ScaleOut StateServer service and easily scale the size of the distributed store to meet the needs of your application. ScaleOut Software has released publicly available Linux Amazon Machine Images that are pre-configured with the ScaleOut StateServer daemon, and ScaleOut StateServer’s management tools have been enhanced to simplify the deployment and management of AWS virtual machine instances. ScaleOut StateServer on AWS allows you to take advantage of cost-effective, pay-as-you-go pricing, so you pay only for the resources you need while allowing flexibility during periods of atypically high or low load. Visit http://www.scaleoutsoftware.com/evaluate-purchase/pricing/ for the most up-to-date pricing details.
Terminology
The following terms defined by Amazon Web Services are used in this help file and defined here for your convenience:
Amazon Machine Image (AMI): Amazon Machine Images are machine images stored within Amazon’s infrastructure. An AMI contains the operating system and other software such as ScaleOut StateServer. A pre-packaged AMI that is configured with ScaleOut StateServer is available in the AWS Marketplace.
Instance: An instance represents a single running copy of an Amazon Machine Image (AMI).
Region: Amazon EC2 allows you to run EC2 instances in multiple geographic locations called regions. When deploying your ScaleOut StateServer instances, it is highly recommended that you select a region with the closest geographical proximity to the majority of your WAN traffic, if applicable.
Availability Zone: Every AWS region comprises two or more isolated units of failure within the Amazon Web Services environment called availability zones. A failure in one availability zone is unlikely to propagate to other availability zones within the same region. Resources within the same availability zone will experience lower average network latency than resources that cross availability zones.
Key Pair: A key pair is a public-key, private-key encryption system used by Linux-based instances for authentication when logging in to the systems via SSH. A key pair consists of a public key and a private key, and the matching key must be provided to authenticate against a running EC2 instance. An instance may have only one key pair defined at launch, and it may not be changed after launch. An instance without a key pair defined at launch will not be able to grant authentication for advanced administration via remote SSH login.
Private IP: A private IP address belongs to a single instance and is only routable from within the instance’s associated EC2 Region. Data transfer fees do not apply to data transferred using private IP addresses. When operating within the same EC2 region, use of the private IP Address is preferred to avoid data transfer fees.
Public IP: A public IP address belongs to a single instance and is routable from within the EC2 environment, including from other EC2 regions, and from external, Internet locations.
Elastic IP (EIP): An Elastic IP (EIP) is a fixed (static) public IP address allocated through EC2 and assigned to a running virtual machine instance. Elastic IPs exist independently of virtual machine instances and may be attached to only a single instance at a time, but they may be reassigned to different instances with complete transparency to end users. If an Elastic IP is associated with an instance, it invalidates and overrides the original public IP.
Security Group: A security group is a named set of allowed inbound network connection rules for EC2 instances. Each security group consists of a list of protocols, ports, and source IP address ranges. A security group can apply to multiple instances, and an instance can be a member of multiple security groups. Security groups may only be assigned to an instance when the instance is being launched. Changes to a security group’s allowed inbound network connections apply to all instances assigned to that Security Group.
Placement Group: A cluster placement group is a logical entity that enables creating a cluster of instances with special characteristics, such as high speed networking. Using a placement group, a cluster of instances can have low latency, 10 gigabit Ethernet bandwidth connectivity between instances in the cluster.
Prerequisites
To deploy ScaleOut StateServer in AWS, begin by visiting http://aws.amazon.com/ and signing up for an AWS account.
ScaleOut’s management tools require a set of access credentials to perform actions in AWS on your behalf. In Amazon Web Services, these credentials are referred to as Access Keys. To retrieve or configure Access Keys for your account, visit the Security Credentials page in the AWS site. Next, record the Access Key ID and the Secret Access Key to be used by ScaleOut StateServer management tools.
Note
Credentials defined on this page have full account privileges (“root credentials”) and are recommended for debugging and initial testing only. For production environments or where security is a concern, use the AWS Identity and Access Management (IAM) feature to create security-limited credentials. When creating an IAM security policy, the following permissions are required:
IAM Permission |
Requirement |
|---|---|
ec2:AllocateAddress |
Required to create a new Elastic IP addresses. |
autoscaling:CreateAutoScalingGroup |
Required to create new Auto Scaling Groups for clustered instances during stack creation. |
autoscaling:CreateLaunchConfiguration |
Required to create new Launch Configurations for clustered instances during stack creation. |
autoscaling:DeleteAutoScalingGroup |
Required to delete automatically created Auto Scaling Groups for clustered instances during stack deletions. |
autoscaling:DeleteLaunchConfiguration |
Required to delete automatically created Launch Configurations for clustered instances during stack deletions. |
autoscaling:DeleteLifecycleHook |
Required to delete automatically created Lifecycle Hooks for Auto Scaling Groups during stack deletions. |
autoscaling:DescribeAutoScalingGroups |
Required to retrieve Auto Scaling Groups during scale in or scale out requests. |
autoscaling:DescribeLaunchConfigurations |
Required to retrieve Launch Configurations during stack creation, scale in, or scale out requests. |
autoscaling:DescribeLifecycleHooks |
Required to retrieve Lifecycle Hooks during stack creation, scale out, or scale in requests. |
autoscaling:DescribeScalingActivities |
Required to retrieve Scaling Activities during stack creation, scale out, or scale in requests. |
autoscaling:PutLifecycleHook |
Required to create new Lifecycle Hooks for Auto Scaling Groups during stack creation. |
autoscaling:UpdateAutoScalingGroup |
Required to update Auto Scaling Groups during scale up or scale down requests to launch or terminate EC2 instances. |
cloudformation:CreateStack |
Required to create new CloudFormation Stacks during stack creation. |
cloudformation:DeleteStack |
Required to delete CloudFormation Stacks during stack deletions. |
cloudformation:DescribeStacks |
Required to retrieve the configuration for existing CloudFormation Stacks. |
cloudformation:UpdateStack |
Required to update CloudFormation Stacks during scale out or scale in requests. |
ec2:AssociateRouteTable |
Required to associate Route Tables to VPCs during stack creation. |
ec2:AttachInternetGateway |
Required to attach Internet Gateways to VPCs during stack creation. |
ec2:AuthorizeSecurityGroupIngress |
Required to authorize ports for inbound communication during stack creation. |
ec2:CreateInternetGateway |
Required to create new Internet Gateways for VPCs during stack creation. |
ec2:CreatePlacementGroup |
Required to create new Placement Groups for clustered instances to ensure low latency communication. |
ec2:CreateRoute |
Required to create new Routes for Route Tables during stack creation. |
ec2:CreateRouteTable |
Required to create new Route Tables for VPC Subnets during stack creation. |
ec2:CreateSecurityGroup |
Required to create new Security Groups for VPCs during stack creation. |
ec2:CreateSubnet |
Required to create new Subnets for VPCs during stack creation. |
ec2:CreateTags |
Required to launch new EC2 instances (for internal bookkeeping) during stack creation, scale out, or scale in requests. |
ec2:CreateVpc |
Required to create new VPCs during stack creation. |
ec2:DeleteInternetGateway |
Required to delete automatically created Internet Gateways during stack deletion. |
ec2:DeletePlacementGroup |
Required to delete automatically created Placement Groups during stack deletion. |
ec2:DeleteRoute |
Required to delete automatically created Routes for Route Tables during stack deletion. |
ec2:DeleteRouteTable |
Required to delete automatically created Route Tables for VPC Subnets during stack deletion. |
ec2:DeleteSecurityGroup |
Required to delete automatically created Security Groups for VPCs during stack deletion. |
ec2:DeleteSubnet |
Required to delete automatically created Subnets for VPCs during stack deletion. |
ec2:DeleteVpc |
Required to delete automatically created VPCs during stack deletion. |
ec2:DescribeAvailabilityZones |
Required to connect to AWS. |
ec2:DescribeInstances |
Required to retrieve and display information about EC2 instances. |
ec2:DescribeInternetGateways |
Required to retrieve Internet Gateways during stack creation. |
ec2:DescribeKeyPairs |
Required to list available Key Pairs for selection in the ScaleOut Management Console. |
ec2:DescribePlacementGroups |
Required to retrieve Placement Groups during stack creation, scale out, or scale in requests. |
ec2:DescribeRouteTables |
Required to retrieve Route Tables during stack creation. |
ec2:DescribeSecurityGroups |
Required to retrieve Security Groups during stack creation. |
ec2:DescribeSubnets |
Required to retrieve Subnets during stack creation. |
ec2:DescribeVpcs |
Required to retrieve VPCs during stack creation. |
ec2:DetachInternetGateway |
Required to detach automatically created Internet Gateways from VPCs during stack deletion. |
ec2:DisassociateRouteTable |
Required to disassociate Route Tables from VPCs during stack deletion. |
ec2:ModifyVpcAttribute |
Required to configure the automatically created VPC during stack creation. |
ec2:RebootInstances |
Required to reboot running instances. |
ec2:RevokeSecurityGroupIngress |
Required to remove ports from inbound communication of an automatically created Security Group during stack deletion. |
ec2:RunInstances |
Required to launch new EC2 instances during stack creation or scale out requests. |
ec2:TerminateInstances |
Required to terminate EC2 instances as part of a scale in event. |
iam:AddRoleToInstanceProfile |
Required to create the instance IAM role during stack creation. |
iam:CreateInstanceProfile |
Required to create the instance IAM role during stack creation. |
iam:CreateRole |
Required to create the instance IAM role during stack creation. |
iam:DeleteInstanceProfile |
Required to delete the instance IAM role during stack termination. |
iam:DeleteRole |
Required to delete the instance IAM role during stack termination. |
iam:DeleteRolePolicy |
Required to delete the instance IAM role during stack termination. |
iam:GetRole |
Required to create the instance IAM role during stack creation. |
iam:PassRole |
Required to create the instance IAM role during stack creation. |
iam:PutRolePolicy |
Required to create the instance IAM role during stack creation. |
iam:RemoveRoleFromInstanceProfile |
Required to delete the instance IAM role during stack termination. |
sqs:CreateQueue |
Required to create an SQS queue used for scale out or scale in requests. |
sqs:DeleteQueue |
Required to delete the automatically created SQS queue used for scale out or scale in requests. |
sqs:GetQueueAttributes |
Required to create an SQS queue used for scale out or scale in requests. |
Managing AWS Using the ScaleOut Management Console
The ScaleOut Management Console can be used to easily launch and manage Amazon EC2 virtual machine images that are pre-configured with the ScaleOut StateServer service. On your local workstation, run the ScaleOut installer and select the Remote Client/Cloud Mgt. Setup Type, as described in the section Components.
Accessing AWS Management in the Console
After completing the installation wizard, the ScaleOut Management Console will start automatically and will immediately prompt you to configure your connection to a ScaleOut StateServer store. Dismiss this prompt. In the Console’s View menu, toggle the Show AWS Management menu item. This will cause the AWS Management node to appear in the Console’s tree list on the left side of the window:
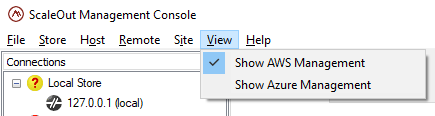
Creating an AWS Connection
To deploy the ScaleOut service to AWS, the ScaleOut Management Console must be configured to establish a connection to AWS. Right click on the AWS Management node in the tree list and select Manage Connections from the context menu. The AWS Connection Management window will appear:
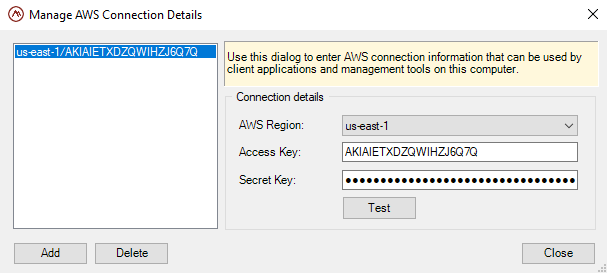
Use this window to define connections to AWS using the credentials that you established earlier in the Deploying in Amazon Web Services topic. If you need to manage ScaleOut stores in multiple AWS regions, you can click the Add button to define more connections for the different regions.
Once the connection details have been entered, close the window and select the AWS Management node on the left side of the Console to open the AWS Management pane in the main area of the window:
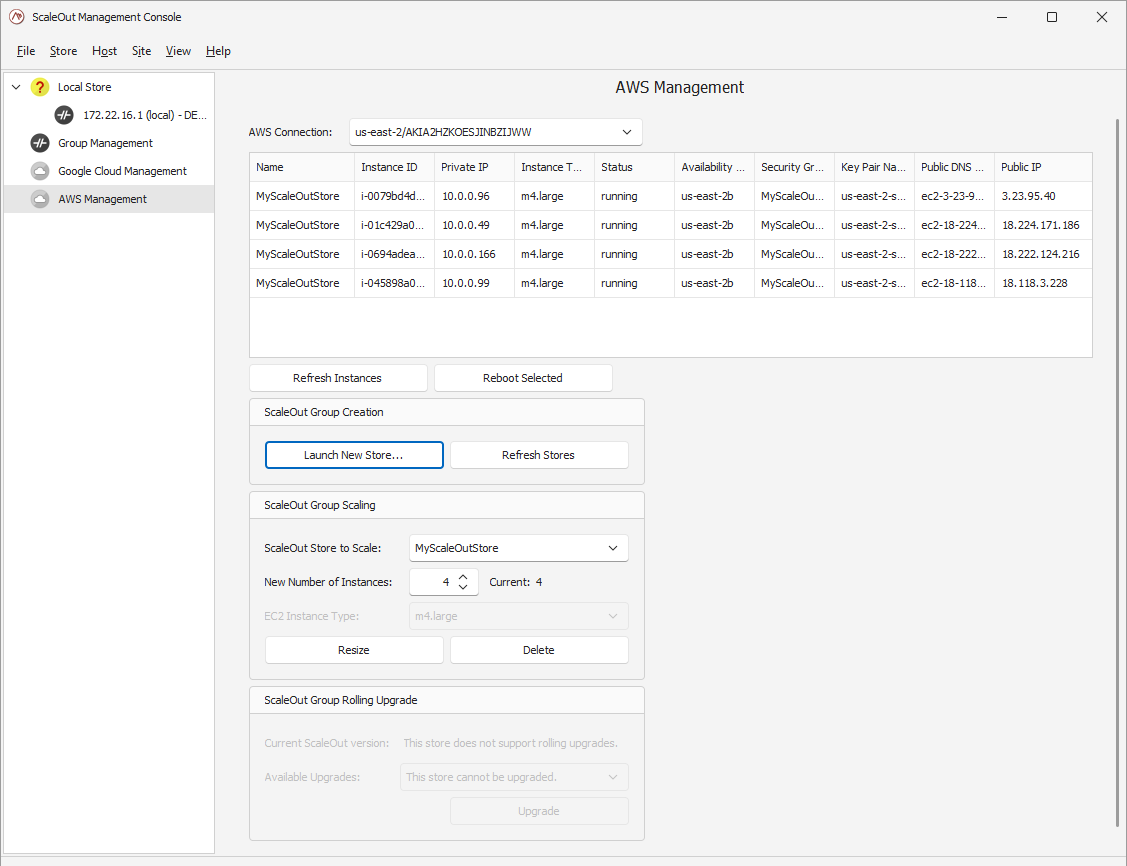
Click the AWS Connection dropdown to connect to AWS using the connection details you have defined. (Note that the Manage Connections dialog also can be launched from this dropdown.)
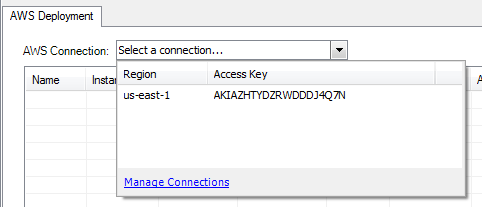
When you select a connection from this dropdown, the ScaleOut Management Console will connect to Amazon Web Services and will display any instances you have running in the current region.
Launching a New ScaleOut Host Group
You are now ready to launch a group of ScaleOut hosts which will form a single ScaleOut store. The ScaleOut management tools take care of all the configuration steps required for the deployed instances to form a single ScaleOut host group. It is only necessary to select a store name, an SSH keypair (used for optional remote login), and decide how many instances to deploy using the Launch New Store wizard. In addition, several configuration options are available to you.
To start the wizard, click the Launch New Store… button in the AWS Management pane. The wizard will automatically open to the summary page, where the name of the store, the SSH keypair, and the count of the EC2 instances are the only three required fields:
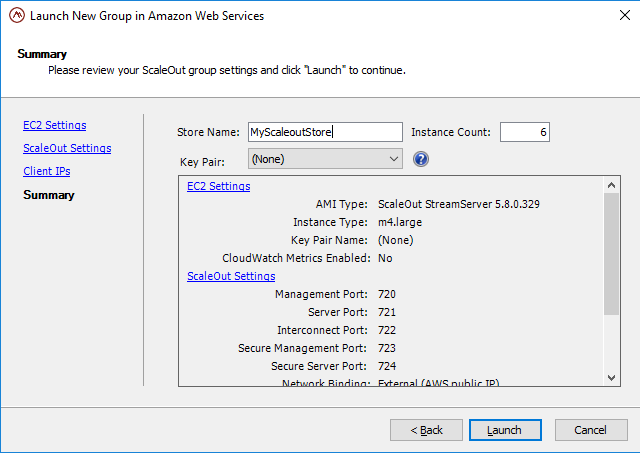
Prior to clicking the launch button, however, you may want to review the other pages in the wizard to confirm that the default selections are acceptable.
The EC2 Settings page allows you to fine-tune the Amazon EC2 settings for the instances that you are about to launch:
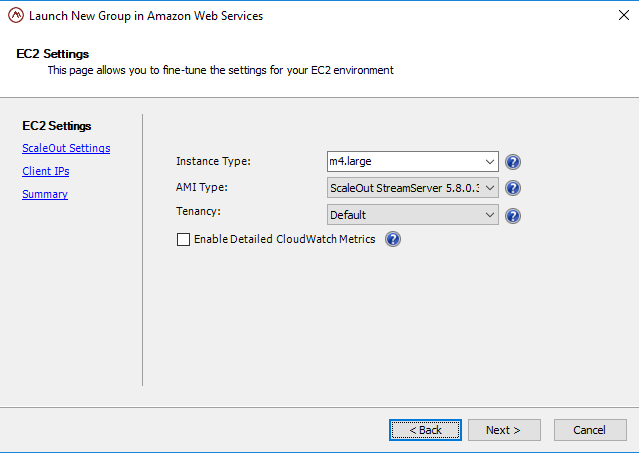
The following settings may be adjusted from this page:
Instance Type: An instance type defines the memory, CPU, storage capacity, and hourly cost for an instance. Specify the size of the instances that you will be launching.
AMI Type: Select the Amazon Machine Image that you would like to launch. The AMIs listed here are provided by ScaleOut Software and run the ScaleOut StateServer service. Use of the latest version is recommended.
Tenancy: The physical tenancy of the launched instances. An instance with ‘dedicated’ tenancy runs on single-tenant hardware at an additional cost (billed by Amazon).
Enable Detailed CloudWatch Metrics: If checked, adds additional ScaleOut StateServer-related metrics to Amazon CloudWatch, which can be used for monitoring or alarms.
The ScaleOut Settings lets you specify the ports used by the ScaleOut StateServer service (daemon). Use of the default ports is recommended.
The Service Network Binding lets you specify whether the ScaleOut hosts should use their public or private IP address as their advertised gateway.
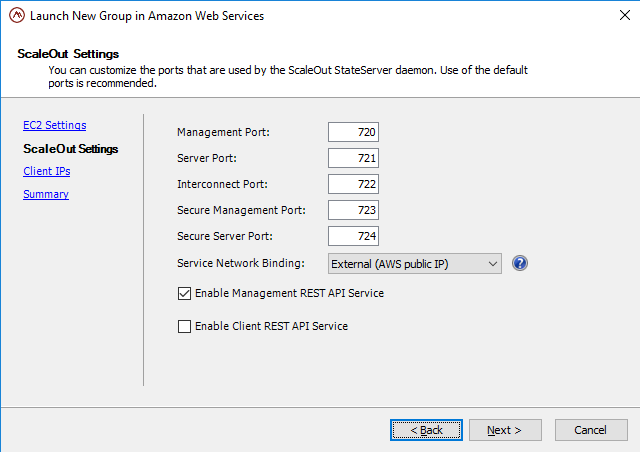
Additionally, you can enable the Web-based management console from this page. Checking the Enable Management REST API Service box will enable the ScaleOut Management REST API Service to be started by default, and will open port 4000 to any clients specified on the following Client IPs page. Similarly, checking the Enable Client REST API Service box will enable the ScaleOut Client REST API Service to be started by default, and will open port 4000 to specified clients.
The Client IPs page lets you specify the IP addresses that may access your instances. An EC2 security group will not allow network access to the instances you are launching unless you specifically provide it with a white list of allowed client IP addresses.
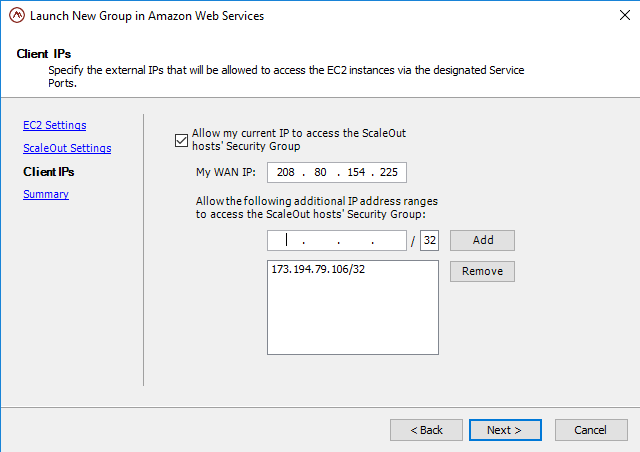
By default, the wizard grants access to the external WAN IP of your local system. (Your external IP is determined by a quick request to an external “What’s My IP?” Web service operated by ScaleOut Software. No personal information is logged when determining your WAN IP.) If you have additional ranges of IP addresses that will need access to the ScaleOut store, they can be specified on the Client IPs page using CIDR notation.
After completing the Launch New Store wizard, you can launch the new ScaleOut host group from the wizard’s summary page using the Launch button. A status window will appear as resources are created in the AWS environment. Once completed, you can close the wizard; the new instances should now be visible in the Console’s AWS Management pane.
Note
It may take several minutes to launch a ScaleOut host group in Amazon Web Services because several AWS resources must be created and configured before the instances boot their operating systems and configure the ScaleOut service to form a cohesive host group.
Immediately after launch, the ScaleOut Management Console will prompt you to connect to the newly launched host group so that you can manage it identically to an on-premise host group:
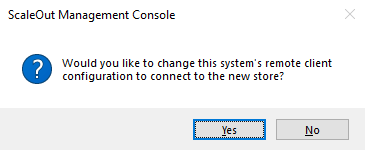
Managing and Scaling ScaleOut Host Groups Deployed in AWS
The AWS Management pane shows you the instances that have been launched for a specified AWS connection. For each instance, several attributes are displayed, including the ScaleOut store name, instance ID and type, private and public IPs, availability zone, security group, key pair name, and public DNS name. You can refresh the table of instances using the Refresh Instances button to see the latest information. You also can reboot selected instances as described below.

You can reboot selected instances if necessary by selecting the instances and then clicking the Reboot Selected button.
To add or remove instances to or from a ScaleOut host group, fill out the fields in the ScaleOut Group Scaling box:
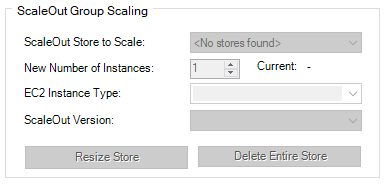
The fields are as follows:
ScaleOut Store to Grow: Select the name of the ScaleOut store that you’d like to add instances to. This field will be disabled if you do not have an existing store.
New Number of Instances: Specify the total number of desired instances to trigger a scale out or scale in request.
EC2 Instance Type: Read-only. Displays the instance type used for this deployment, which defines the memory, CPU, storage capacity, and hourly cost for an instance.
ScaleOut Version: Read-only. Displays the selected AMI used for this deployment.
After filling out the fields, click the Resize Store button to add or remove EC2 instances to or from the specified ScaleOut store. A status window will appear and will report progress as instances are started in the AWS environment.
Lastly, you can terminate an entire deployment by selecting its store name in the ScaleOut Group Scaling box and clicking Delete Entire Store.
Warning
This option is irreversible and will result in complete data loss of all objects stored in the data grid!
Performing a Rolling Upgrade on an Existing ScaleOut Host Group
The latest Management Console supports rolling upgrades on an existing ScaleOut group of hosts. If a compatible version of the ScaleOut Product Suite exists, you will see the option to upgrade your cluster automatically in the AWS Management pane. Pick the version you want from the combo box, and click on Upgrade.
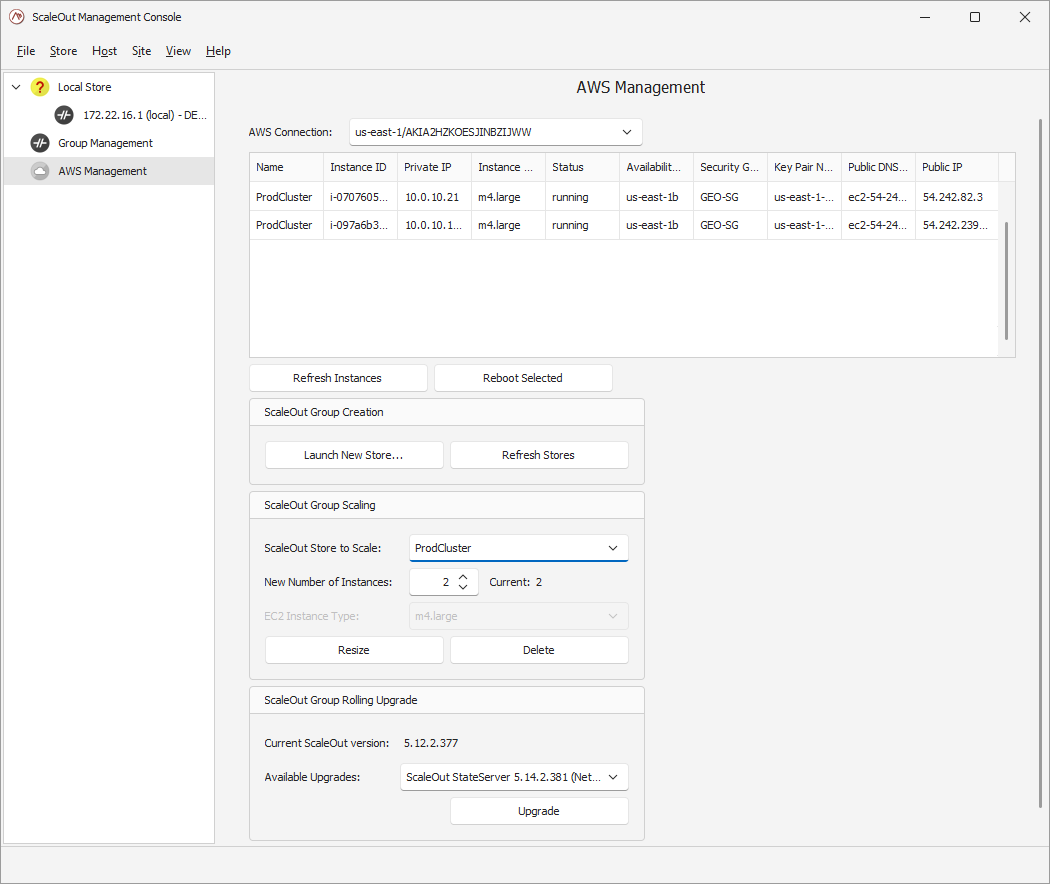
If your cluster uses an older version of the ScaleOut Product Suite, rolling upgrades may not be supported. The Management Console displays all supported versions for the specific product. If you are already using the latest version, the rolling upgrade option will be disabled.
Note
The rolling upgrade process takes time to complete. Each instance of the cluster will successively leave the cluster and be replaced by a new instance running the new version before being terminated. At some point, you may see more instances running at the same time than the desired capacity. That is expected as AWS allows for some time to shutdown each instance cleanly and make sure that the transition completes smoothly.
Managing AWS Using the SOSS Command-Line Control Program
The command-line control program, soss_aws_actions.py, encapsulates all the logic necessary to launch and manage a ScaleOut store running in the Amazon AWS environment.
This command line control program requires Python 2.6 or greater and the Amazon Python library, boto, which is available through the Python package management utilities pip and easy_install, or may also be installed directly from https://github.com/boto/boto. For Linux-based operating systems, boto may be available in your distribution’s software repository.
The command-line syntax for soss_aws_actions.py is as follows:
soss_aws_actions.py command arguments [options]
where the commands are:
create_groupCreate a new host group.
add_instancesAdd new instances to an existing group.
read_gatewaysPrint gateway information for an existing host group.
list_groupPrint instance information for an existing host group.
terminateTerminate a single instance or existing host group.
helpDisplay helps information.
Each command has its own set of required arguments and optional parameters as follows:
create_group
The command-line syntax to create a new ScaleOut host group is as follows:
soss_aws_actions.py create_group [-h]
[--access-key ACCESS_KEY]
[--secret-key SECRET_KEY]
[--region REGION]
[--avail_zone AVAIL_ZONE]
[--version VERSION]
[--security_groups SECURITY_GROUPS [SECURITY_GROUPS ...]]
[--key_pair KEY_NAME]
[--client CLIENT [CLIENT ...]]
[--eip_none | --eip_existing | --eip_new]
[--pub_mgt_port PUB_MGT_PORT]
[--pub_svr_port PUB_SVR_PORT]
[--pvt_mgt_port PVT_MGT_PORT]
[--pvt_svr_port PVT_SVR_PORT]
[--pvt_int_port PVT_INT_PORT]
[--placement_group PLACEMENT_GROUP]
store_name num_instances instance_type
where the arguments and options are:
ACCESS_KEYAccess Key ID used for administrative AWS operations. If not specified, will attempt to read from boto config.
SECRET_KEYSecret access key paired with above access key ID. If not specified, will attempt to read from boto config.
REGIONAWS EC2 region to connect to and query. If not specified, will attempt to read from boto config (default: us-east-1).
store_nameName for the new AWS ScaleOut Store (must be unique)
num_instancesNumber of instances to launch
instance_typeThe type of the instance to launch
AVAIL_ZONEAWS EC2 availability zone in which to launch the new AWS host group (default: no preference)
VERSIONScaleOut version to install, for example 5.0.3.203. If not specified, use latest version.
SECURITY_GROUPAWS Security Group Name in which to launch the new ScaleOut host group. If not specified, create and configure a new Security Group. The Security Group will be modified to support internal communication between instances.
ADDITIONAL_GROUPSAWS Security Group Name(s) in which to launch the new ScaleOut host group. These groups are not modified.
KEY_NAMEAWS Key Pair name to allow you to securely connect to your instance after it launches (default: None)
CLIENTClient access source(s) to add to the Security Group. These sources may be single IP addresses, IP ranges in CIDR format (e.g., 10.11.12.0/24), or the name or unique ID of an existing Security Group (e.g., “My Web Farm” or sg-01234567). Additionally, “localhost” may be specified to determine and add the public-facing IP of the localhost as a client (recommended for management access).
--webInstall the ScaleOut Web Management Console on the launched instance(s). This option installs Apache and PHP on the instance and configures the ScaleOut Web Management Console on http://INSTANCE/soss_mgt. If specified, port 80 will be opened to the client access source(s) specified by the –client option in the primary Security Group.
--eip_noneNo Elastic IPs will be allocated or assigned (default).
--eip_existingAssign existing Elastic IPs if available.
--eip_Allocate new Elastic IPs and assign them.
PUB_MGT_PORTPublic management port (default: 720).
PUB_SVR_PORTPublic server port (default: 721).
PVT_MGT_PORTPrivate management port (default: 720).
PVT_SVR_PORTPrivate server port (default: 721).
PVT_INT_PORTPrivate interconnect port (default: 722).
PLACEMENT_GROUP(Cluster Compute instances only) AWS Placement Group Name in which to launch the new ScaleOut host group. If not specified, create a new Placement Group.
Examples:
Create a new ScaleOut host group of 20 m2.4xlarge instances with the name “MySOSSGroup”, and allow a pre-existing Security Group with the id “sg-01234567” to access the private ScaleOut ports:
soss_aws_actions.py create_group MySOSSGroup 20 m2.4xlarge --access-key=MY_ACCESS_KEY --secret-key=MY_SECRET_KEY --client sg-01234567
As above, but launch in the us-west-1 Region, in the us-west-1b Availability Zone, specifies the “my_ssh_key_pair” as the SSH authentication key pair name, attempt to allocate a new Elastic IP for each instance (maximum of 5 by default), launch the instances into an existing “ScaleOut” Security Group as its primary group, and add the “default” group as a secondary Security Group:
soss_aws_actions.py create_group MySOSSGroup 20 m2.4xlarge --access-key=MY_ACCESS_KEY --secret-key=MY_SECRET_KEY --client sg-01234567 --region us-west-1 --avail-zone us-west-1b --key_pair my_ssh_key_pair --eip_new --security_group "ScaleOut" --additional_groups "default"
add_instances
The command-line syntax to add instances to an existing ScaleOut host group is as follows:
soss_aws_actions.py add_instances [-h]
[--access-key ACCESS_KEY]
[--secret-key SECRET_KEY]
[--region REGION]
[--version VERSION]
[--web]
[--eip_none | --eip_existing | --eip_new]
store_name num_instances instance_type
where the arguments and options are defined above. If specified, the region parameter must be the same region into which the ScaleOut host group was launched.
Example: Adding 3 m1.large instances to the “MySOSSGroup” ScaleOut group:
soss_aws_actions.py add_instances MySOSSGroup 3 m1.large --access-key=MY_ACCESS_KEY --secret-key=MY_SECRET_KEY
read_gateways
The command-line syntax to display gateway information for an existing ScaleOut host group is as follows:
soss_aws_actions.py read_gateways [-h]
[--access-key ACCESS_KEY]
[--secret-key SECRET_KEY]
[--region REGION]
store_name
where the arguments and options are defined above. If specified, the region parameter must be the same region into which the ScaleOut host group was launched.
Example: List the gateway information for the “MySOSSGroup” ScaleOut group:
soss_aws_actions.py read_gateways MySOSSGroup --access-key=MY_ACCESS_KEY --secret-key=MY_SECRET_KEY
list_group
The command-line syntax to display instance information for all instances in an existing ScaleOut host group is as follows:
soss_aws_actions.py list_group [-h]
[--access-key ACCESS_KEY]
[--secret-key SECRET_KEY]
[--region REGION] [--name] [--pub_ip]
[--pub_dns] [--status] [--avail_zone]
[--security_groups] [--key_pair]
store_name
where the arguments and options are defined above. If specified, the region parameter must be the same region into which the ScaleOut host group was launched.
By default, the following information is displayed: Instance ID, Private IP, Instance Type, ScaleOut Version. Additional information may be displayed for each instance by specifying the following optional parameters; columns are displayed in the order that the parameters are specified.
--nameAWS Name tag
--pub_ipPublic IP
--pub_dnsPublic DNS
--statusStatus
--avail_zoneAvailability Zone
--security_groupsSecurity Group(s)
--key_pairSSH Key Pair Name
Examples:
List the default instance information for the “MySOSSGroup” ScaleOut host group:
soss_aws_actions.py list_group MySOSSGroup --access-key=MY_ACCESS_KEY --secret-key=MY_SECRET_KEY
List additional instance information for the “MySOSSGroup” ScaleOut group (Instance ID, Private IP, Instance Type, ScaleOut Version, AWS Name tag, Public DNS):
soss_aws_actions.py list_group MySOSSGroup --access-key=MY_ACCESS_KEY --secret-key=MY_SECRET_KEY --name --pub_dns
terminate
The command-line syntax to terminate an instance or existing ScaleOut host group is as follows:
soss_aws_actions.py terminate [-h]
[--access-key ACCESS_KEY]
[--secret-key SECRET_KEY]
[--region REGION]
{--store_name STORE_NAME | --instance INSTANCE}
where the arguments and options are defined above. If specified, the
region parameter must be the same region into which the ScaleOut host group
was launched. Either a store name or an instance ID must be specified.
If a store name is supplied, all instances with that ScaleOut store name are
terminated. If an instance ID is specified with the instance
parameter, only the specified instance is terminated.
Example: Terminate all instances in the “MySOSSGroup” ScaleOut group:
soss_aws_actions.py terminate --store_name MySOSSGroup --access-key=MY_ACCESS_KEY --secret-key=MY_SECRET_KEY
Example: Terminate the instance with id “i-01234567”:
soss_aws_actions.py terminate --instance i-01234567 --access-key=MY_ACCESS_KEY --secret-key=MY_SECRET_KEY
Deploying Stores in AWS Using CloudFormation Templates
In addition to the Management Console, ScaleOut Software has released CloudFormation Templates to automate the deployment of StateServer stores in AWS. These templates offer the same parameters as the Management Console but allows you to use the familiar CloudFormation stacks in the AWS console or other automation tools.